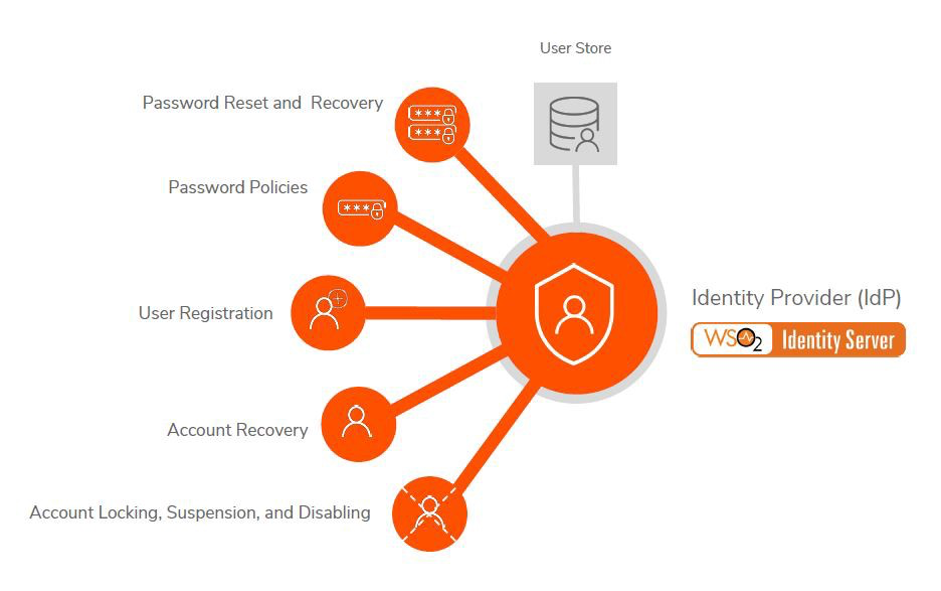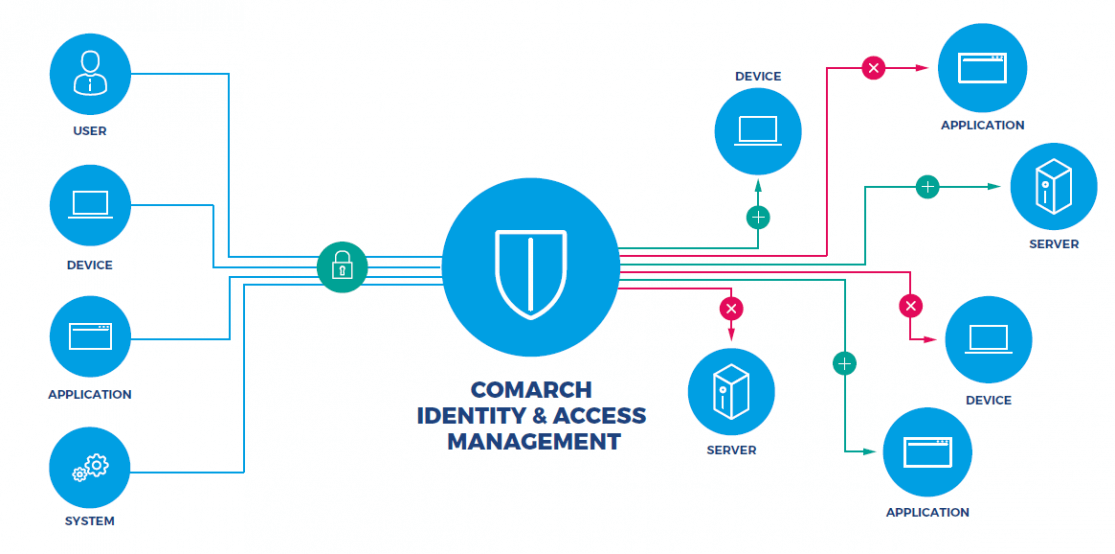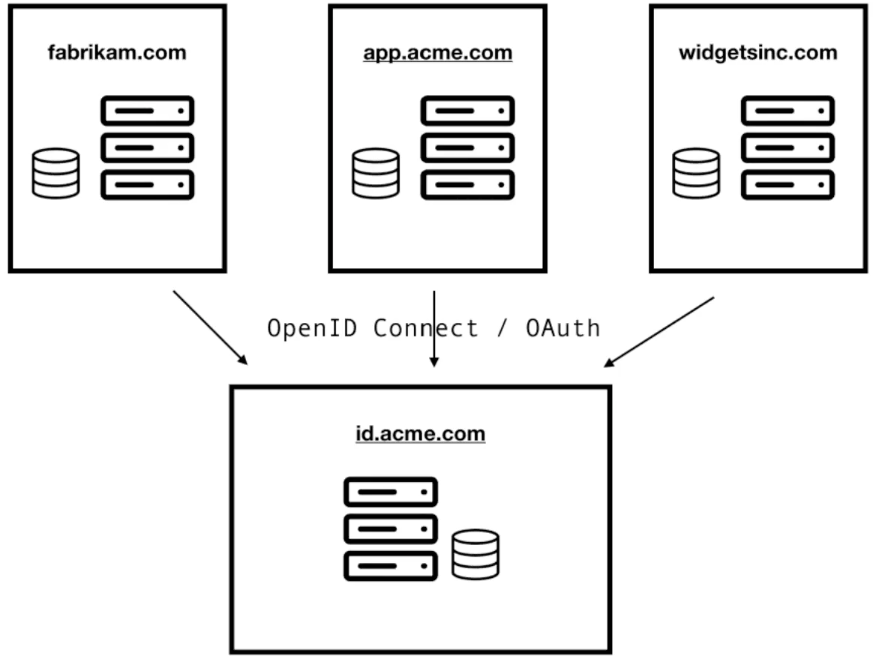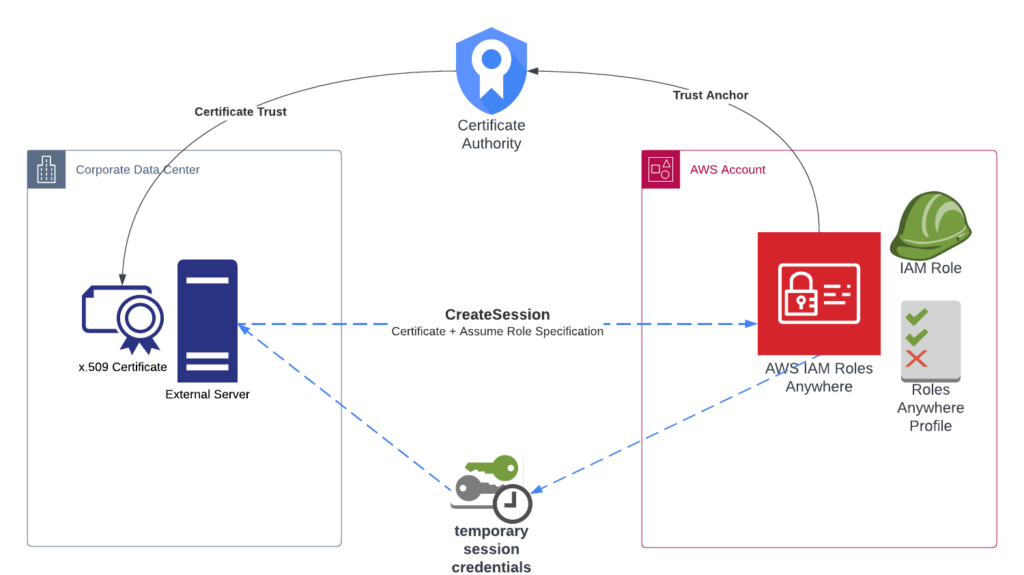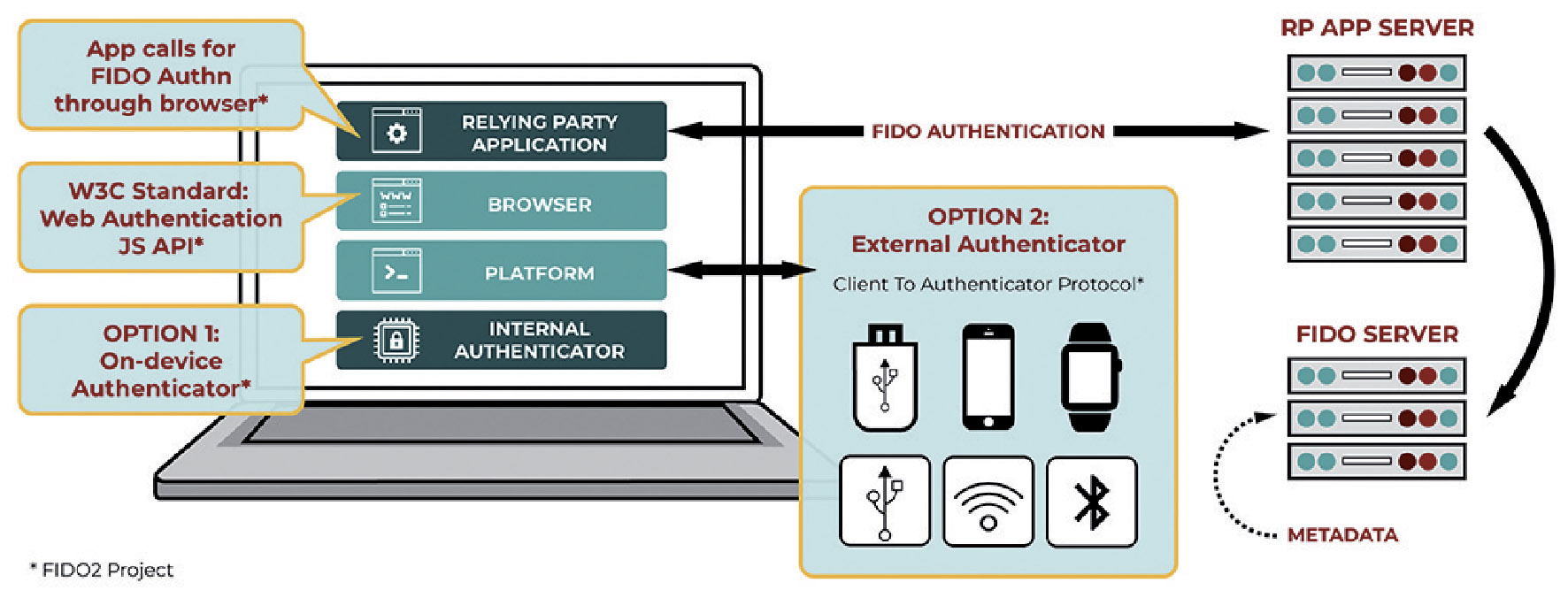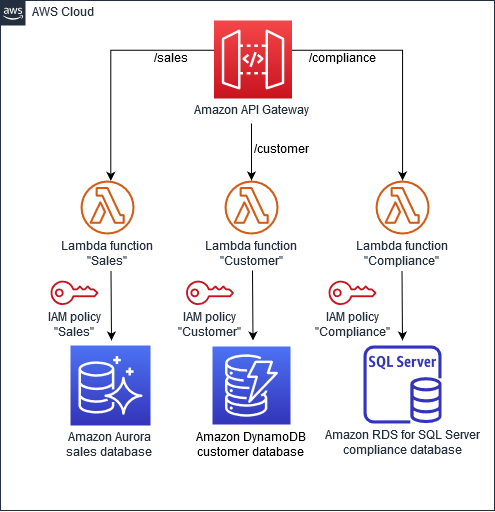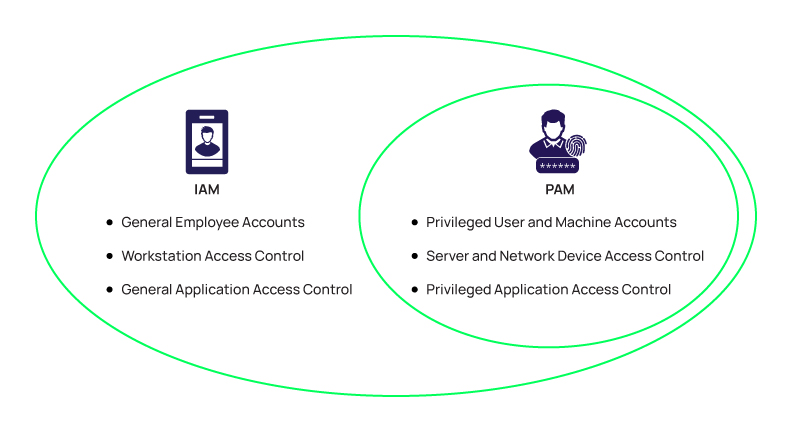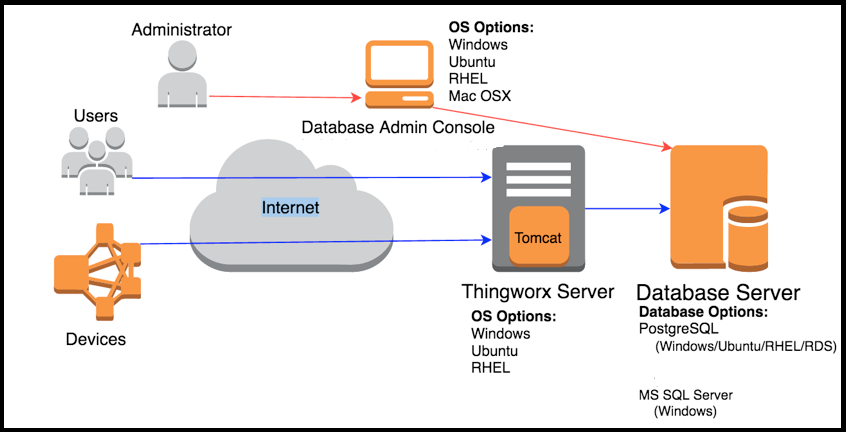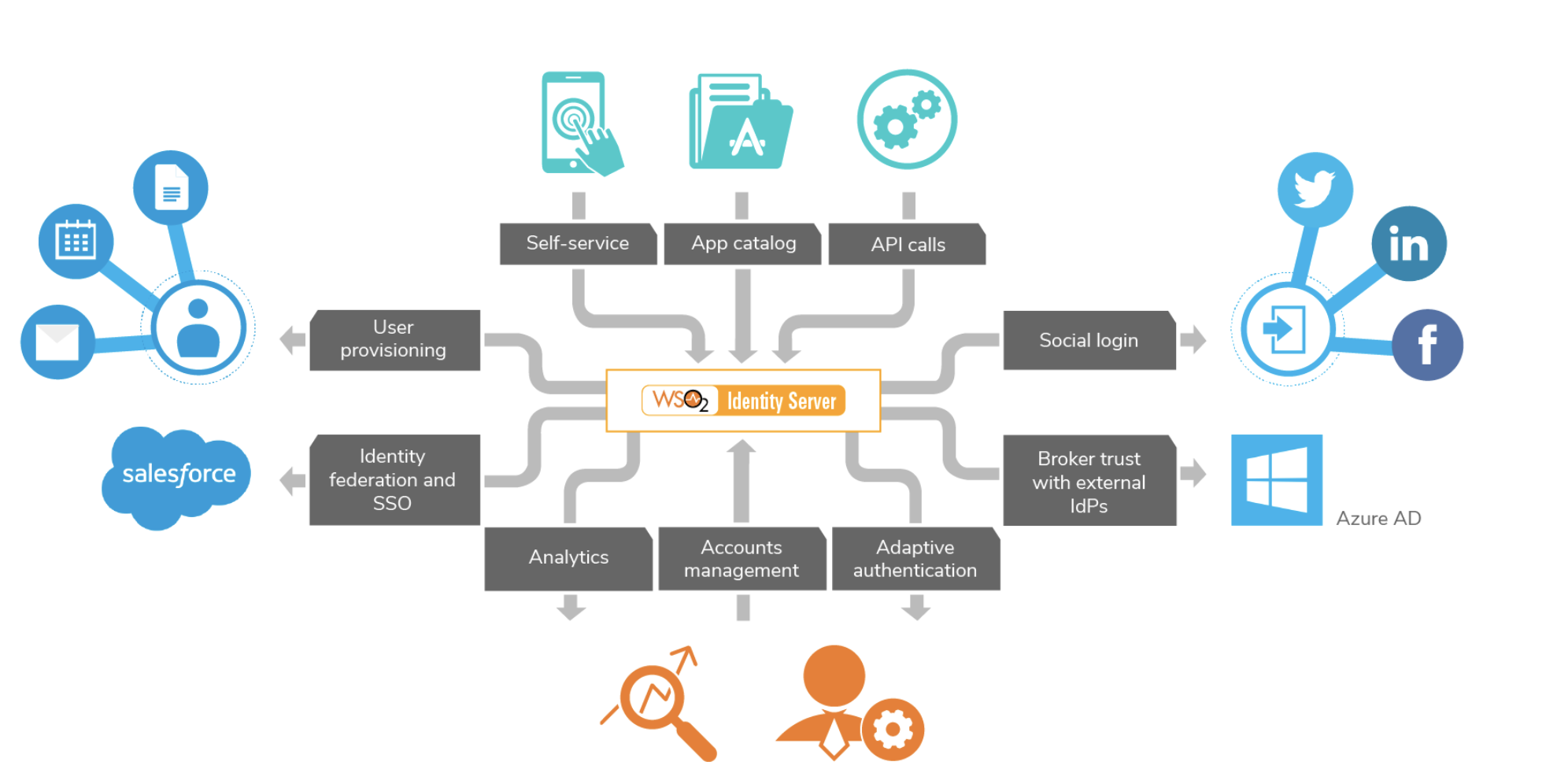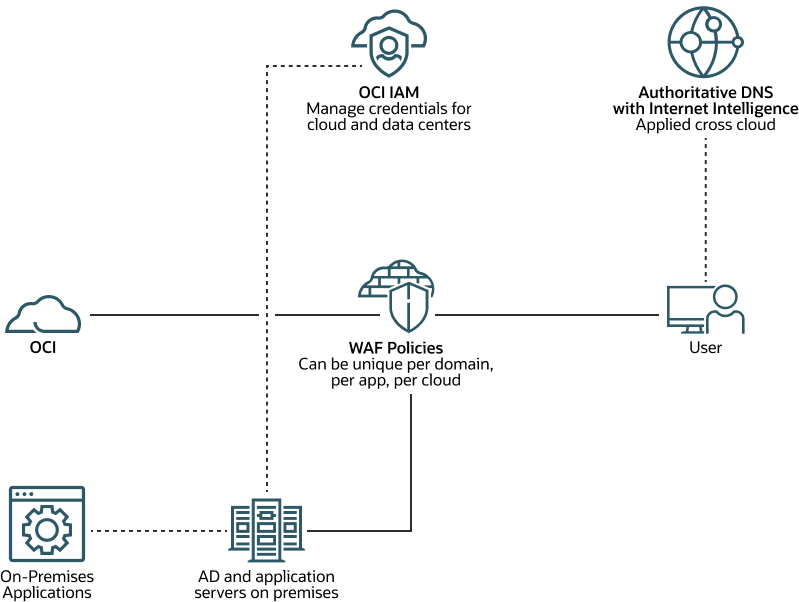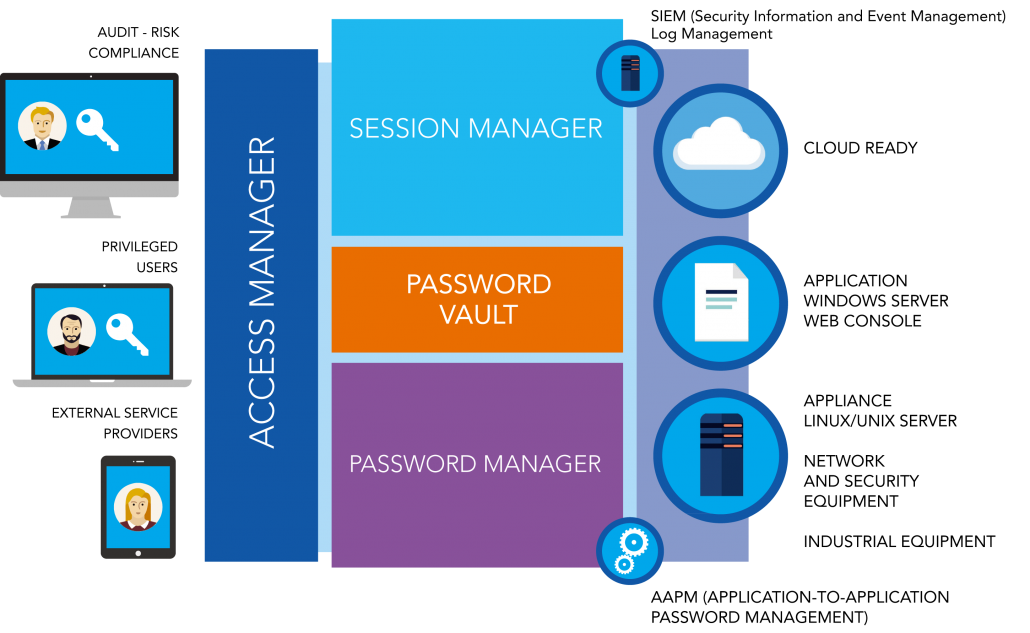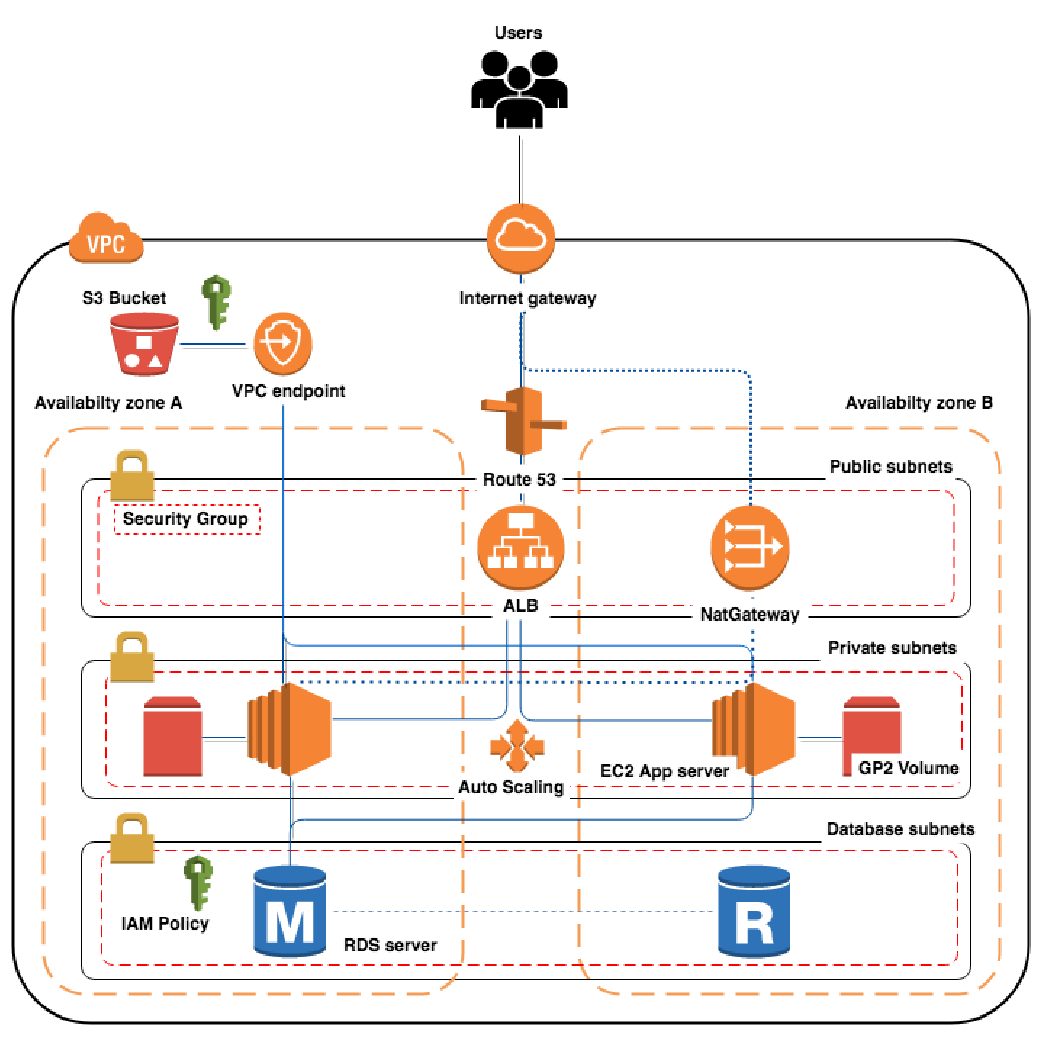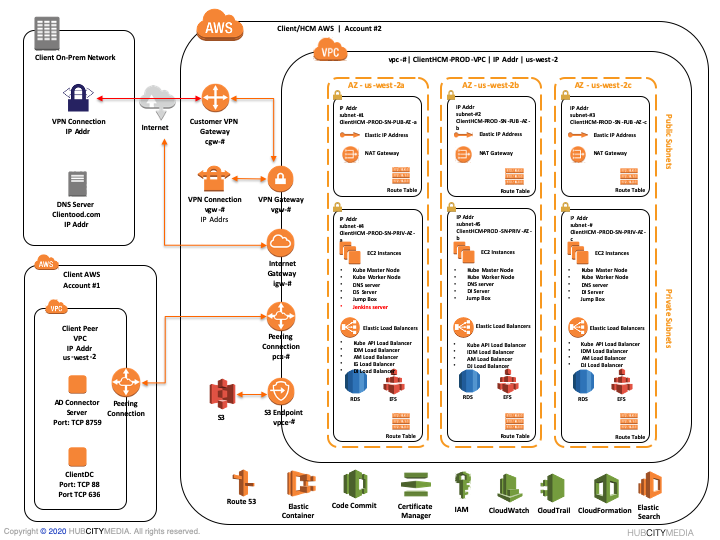
Deploying Identity and Access Management (IAM) Infrastructure in the Cloud - PART 1: PLANNING — HUBCITYMEDIA
About using Amazon IAM roles with NetBackup | About the cloud storage | Veritas NetBackup™ Cloud Administrator's Guide | Veritas™

An overview of the will.iam architecture and its authorization workflow. | Download Scientific Diagram